
In this article, we will guide you on becoming an expert in how LinkedIn deals with extensions and dispel the myth that automation extensions can be entirely safe. Chrome extensions are widely used by LinkedIn users to enhance their platform interaction, offering efficiency and task automation within LinkedIn.
But even an innocent LinkedIn email finder – or any Chrome extension, even if it is not helping you with LinkedIn – has the potential to cause a warning on your account (we attach the list in the section “Pin it: List of not banned but still unsafe LinkedIn extensions”).
The truth about LinkedIn Scraper & other extensions
The majority of LinkedIn users employ Chrome extensions to enhance their interaction with the platform and increase efficiency. These extensions are crafted to simplify routine tasks and automate targeted activities within LinkedIn.
These tools are very seductive because they can elevate the LinkedIn experience in many possible ways. Let’s briefly review each type that you may use.
LinkedIn lead extractor Chrome extension
It automates the extraction of valuable leads from LinkedIn, allowing you to focus on building relationships and growing your network. For example, you can download transfer leads to your CRM. If you want your LinkedIn leads to be available on Salesforce, this can be done with a Chrome extension.
By the way, Linked Helper now is directly compatible with 3 top CRMs – HubSpot, PipeDrive, and Close.
Download Linked Helper 2
and get 14-day free trial right now
DOWNLOADIf you are not yet in our list of users, then join.
We give you a trial version to start your experience with our LinkedIn tool.
LinkedIn profile scraper Chrome extension
Whether you’re researching competitors, scouting potential collaborators, or simply gathering insights, this scraper extension goes beyond basic details, providing comprehensive data to enhance your decision-making process. A LinkedIn data scraper Chrome extension may help you retrieve profiles with descriptions and download them as a CSV.
Moreover, you may want to install a Sales Navigator LinkedIn extension if you are using this enhanced plan and want to filter leads deeply before scraping (by groups, for example).
LinkedIn contact finder extension
With intelligent algorithms and search optimization, these tools help you discover relevant contact data of professionals in your industry. For example, you can find and copy emails, use LinkedIn to detect a contact number with a finder extension, copy people’s addresses, etc. You can use Linked Helper as an alternative to a LinkedIn extension for email search if you need emails of your 2nd and 3rd degree connections.
LinkedIn booster extension
With features like automated endorsements, connection requests, and content sharing, these tools maximize your reach and ensure that your profile stands out in the competitive LinkedIn landscape. For example, a LinkedIn auto-connect Chrome extension can help you eliminate manual clicks for mass network growth. LinkedIn Message Automation: The Definitive Guide
Other activities
- Content Recommendations: Receive suggestions for topics and headlines, and tips for formatting and layout.
- Customized Scheduling: Create personalized scheduling links directly within LinkedIn messages.
- LinkedIn Hashtags Chrome extension: These tools, seamlessly integrated into your LinkedIn experience, providing real-time suggestions and hashtag analytics. This Chrome extension may visualize the impact of each hashtag.
Read carefully: The pain point
However, there is one caveat – LinkedIn is against such extensions and automation in general, so it is crucial to make a responsible choice of tools. More details can be found in this LinkedIn help article.
In other words, most people using extensions, or at least having them installed in their browsers, are unaware that their LinkedIn accounts are at risk of receiving a warning. This is because LinkedIn monitors lists of installed extensions, not just their usage. Later, we will demonstrate and reveal all these tricks and show how LinkedIn keeps an eye on your activity.
Why should you trust the info below?
Linked Helper has been a steadfast companion in the realm of LinkedIn automation since October 2016. Whether you’re a seasoned user of our software or you just stumbled upon this article, you now have the exclusive opportunity to delve into the world of secure automation with our standalone software, absolutely free for a 14-day trial.
With years of honed expertise in software development and a dedicated user base exceeding 300K, we initially rose to prominence as the premier extension in the Chrome Store for LinkedIn automation, reigning supreme from 2016 to August 2019. Our extensive experience uniquely positions us to effectively bypass automation detection on LinkedIn.
The departure of Linked Helper 1 (the extension) from the Chrome Store in August 2019
This event was prompted by LinkedIn’s heightened vigilance in detecting Chrome extensions. This detection challenge stemmed from the facts that:
- When the app is in the Chrome Store, LinkedIn can discern the extension’s ID during installation.
- Chrome Store policies, with their insistence on open and static code, rendered extensions susceptible to detection.
Crucially, it’s worth noting that Linked Helper’s Chrome extension weathered two successive waves of LinkedIn’s mass extension detection.
So… In response to these challenges, and to ensure our users could seamlessly continue their LinkedIn prospecting endeavors, we developed a new iteration.
Since 2020 (with a public beta in March and an official release in December), Linked Helper 2 stands as a supremely secure standalone version, adeptly addressing the pitfalls associated with Chrome extensions. This standalone iteration has demonstrated resilience against LinkedIn’s sweeping waves of mass detection.
Now, with Linked Helper as software, you can not only automate various actions but also scrape data from prospects and directly transfer it to top CRMs. For instance, you can securely get email addresses from LinkedIn without having to connect with individuals or install any questionable Chrome extensions. Explore Linked Helper vs. Octopus CRM 2023: Which Is the Best LinkedIn Tool?, Linked Helper vs. Dux-Soup 2023: Which is the Best LinkedIn Tool?
Insider hacks on LinkedIn’s extension detection
LinkedIn employs two distinctive methods for detecting the use of extensions, accompanied by behavioral analysis. Understanding these methods is crucial for the secure use of extensions!
Method #1
Think of a LinkedIn JavaScript code in your web browser as an astute detective, actively scouring its interface for clues. It diligently examines the browser data, identifying indications of browser extensions and discreetly compiling a list. Although these checks look somewhat rudimentary, they may be effective in their simplicity.
The algorithm goes through local files, making local requests to unique resources associated with the extensions LinkedIn does not approve. Armed with information about each prohibited extension ID from the Chrome Store and associated file, it gathers pertinent data and makes matches between local data found and the list of extension IDs and correlated files. This compilation is then surreptitiously sent to LinkedIn’s server for further analysis.
To put it simply, the script checks whether the prohibited extension logo is there, meaning the extension is installed.
Method #2
LinkedIn later introduced a smarter algorithm, similar to a clever detective. This algorithm, known as a Web Worker, regularly activates in the background of the webpage. It carefully examines tags without text-like content, extracting script and style tags along with their content. After encrypting this information, it sends the encrypted data to LinkedIn’s server, acting like a detective that analyzes it to uncover any signs of hidden browser extensions.
This article focuses exclusively on the first type of detection. For detailed insights, refer to the article here.
3 Disillusioning realities about extensions and LinkedIn
- Extensions in Google Chrome have persistent IDs, which can be found in the link leading to the extension in Chrome, or by opening chrome://system/ and expanding the extensions section.
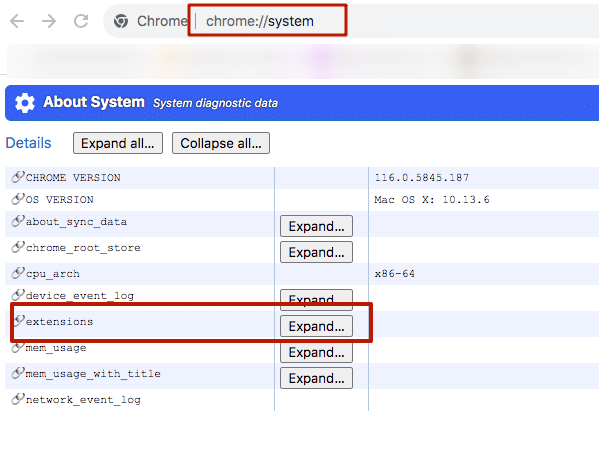
- Extensions locally store certain resources (such as files, for example, a logo file), which can be accessed by knowing the extension’s ID and the filename.
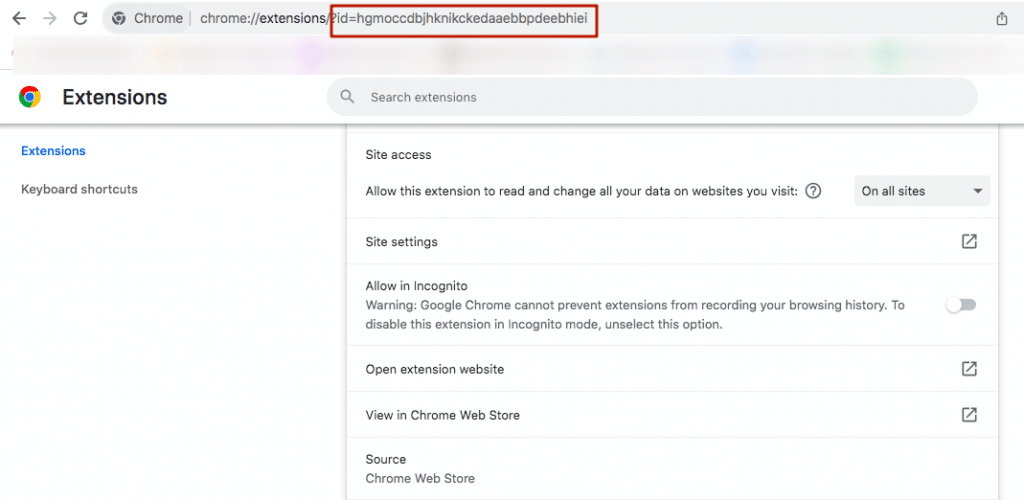
- By using scripts on its pages, LinkedIn can, with access to such resources and knowledge of specific extension filenames, check for the existence of these files through a GET request, thereby confirming the installation of an extension.
Pin it: List of not banned but still unsafe LinkedIn extensions
Note: LinkedIn maintains a non-official list of banned extensions. However, the following compilation is more specialized, highlighting a roster of potentially problematic extensions for LinkedIn. While these extensions may not be officially prohibited, they are considered risky in their nature.
Let’s delve more into practice now! We’ve compiled a document containing the list of bad extensions for LinkedIn.

What you need to know about the tools in the list:
- The inclusion of an extension in the list doesn’t guarantee that LinkedIn can definitively detect it. It simply means that the developers at LinkedIn, who crafted the code, believe they can detect it.
- These are only the extensions that LinkedIn attempts to detect on the client side. LinkedIn also employs a server-side detector that analyses snapshots of client pages.
Does the problem really exist?
If you’re skeptical about delving into security concerns about extensions, we’ve gathered some real facts that prompted us to share this information with you:
Examples from our clients’ situations:
Recently, we received several messages from clients about warnings. Upon investigation, it was revealed that all of them had Chrome extensions interacting with LinkedIn in some way. For many, the warnings ceased after removing the extensions.
Situation #1
A former employee of Snov.io (a tool for search, verification, and email outreach, with which we are integrated) experienced warnings while using Linked Helper. After contacting us and conducting investigations, it was discovered that his colleagues were working with LinkedIn accounts in Chrome, where the Apollo extension was installed. After removing it, the warnings stopped.
Situation #2
A recent client from a sales chat used Lempod, an extension for increasing engagement, post views, and likes. He was using the Lempod extension along with Linked Helper on the same LinkedIn account which was causing warnings.
Situation #3
A client on a call with our agent mentioned receiving a warning supposedly for Linked Helper, but it turned out he also had the Phantombuster extension installed. After removal, he continued working without further warnings. He had recently installed Linked Helper and had been using it for just a couple of weeks, so we were skeptical about his statement.
During the call, we learned that both before and after installing Linked Helper, he had tested several other extensions. In other words, he had extensions both before Linked Helper and during its use, with the latest one being the Phantombuster extension.
We share this insider information for the safety of LinkedIn marketing professionals – cases of detection due to extensions are becoming more frequent.
Smart automation users know these facts
Fact #1
Even the mere presence of extensions can lead to warnings, as LinkedIn examines not just automation but also the presence of extensions and other factors.
Fact #2
Even if there are no extensions in Chrome, it doesn’t guarantee an absence of warnings during manual use or when automating only with Linked Helper. This is because:
- Even working with LinkedIn manually can be unsafe.
- Working with LinkedIn and Linked Helper in a way that results in either high overall activity or simultaneous usage can be unsafe (explore our article about simultaneous usage and article about using multiple LinkedIn accounts on one PC).
Revealing the secrets of our investigation
You might be curious about how we compiled this list of extensions. We found code on the LinkedIn page in Chrome that checks for extensions.
This was our investigative plan:
- We opened LinkedIn.
- We opened DevTools in Chrome (Ctrl+Shift+i). On a Mac, you can use the hotkeys ⌥ + ⌘ + I.
- When LinkedIn searches for prohibited extensions in the Console, we often see numerous identical errors.
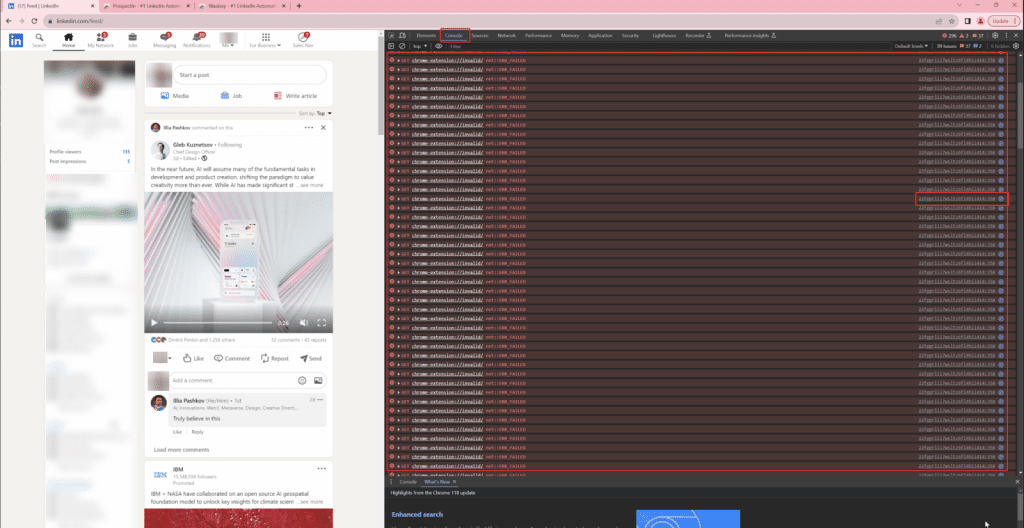
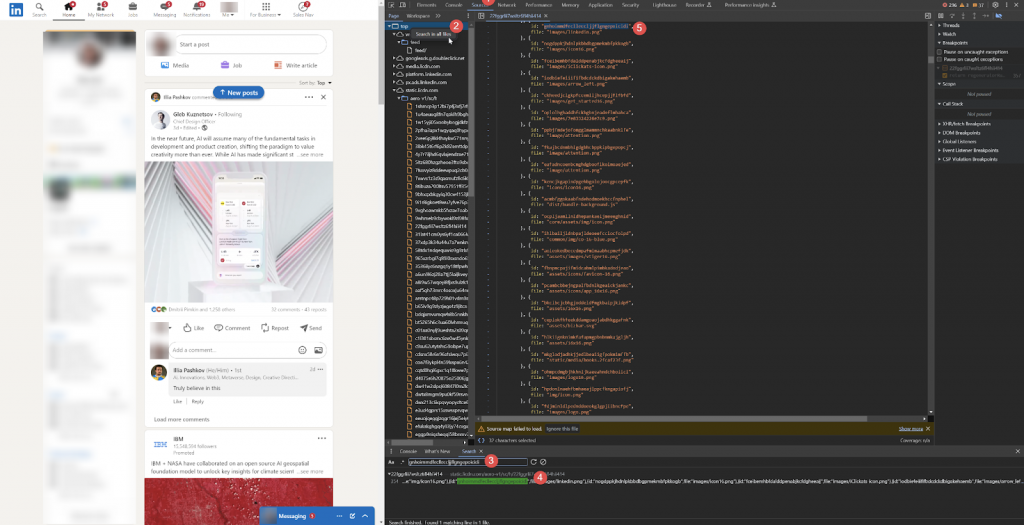
- By clicking on the script name on the right of the error, we opened the LinkedIn page script related to detection. To make the code more readable, we clicked on “Pretty print.”
- Beneath number 2 in the image is the line of code that triggered the error. Here, ${t} is replaced with the extension’s ID, and ${n} is a local file. For example, chrome-extension://agiilkigodfhimkdcjgbjdlajpjdhaig/assets/img/error.png.
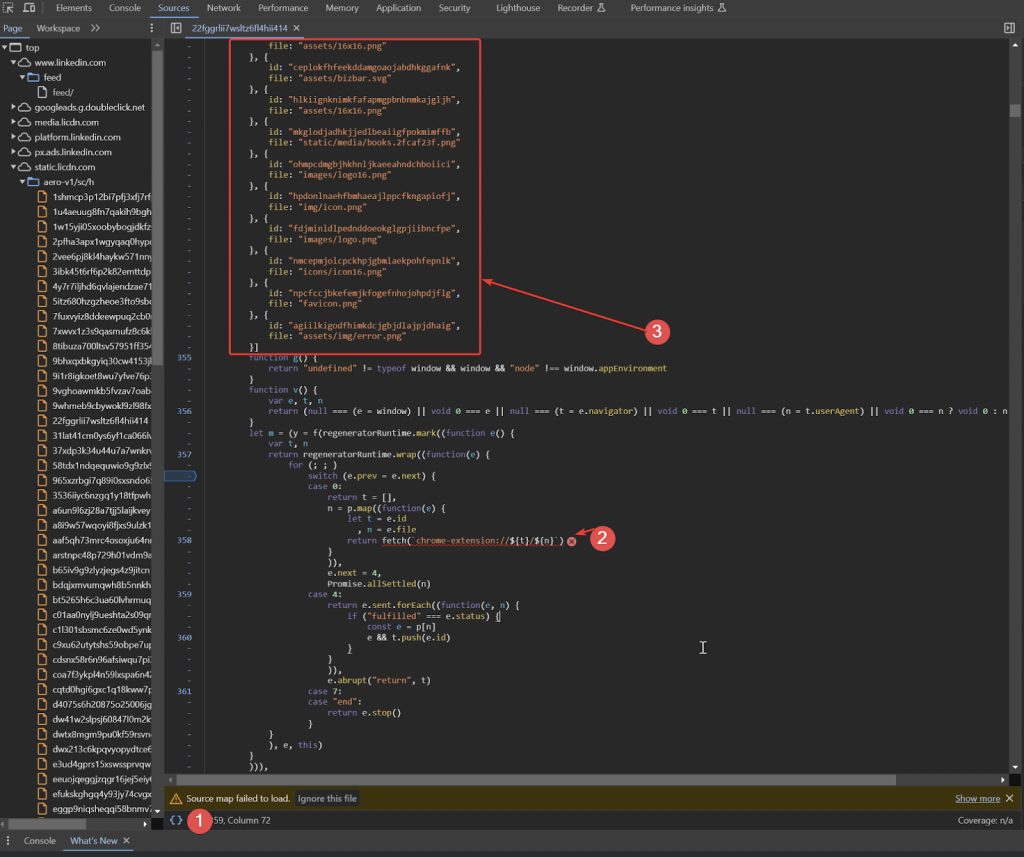
- LinkedIn makes local requests within Chrome to search for files of installed extensions.
- Under number 3 is the list of extensions and their files that LinkedIn is attempting to find.
What did we do?
Taking the array of extension IDs from LinkedIn, we wrote a script that, using these IDs, fetches extension names from the Chrome store. They are presented in an Excel file (below in this section).
Want to perform a basic investigation yourself?
We’ve provided simplified instructions that allow you to check if LinkedIn is indeed hunting for extensions. The risk of such automation is not to be underestimated.
- Open LinkedIn.
- Open DevTools in Chrome (Ctrl+Shift+i) or on Mac (⌥ + ⌘ + I).
- Go to the Sources tab.
- Right-click on Top -> Search in all files.
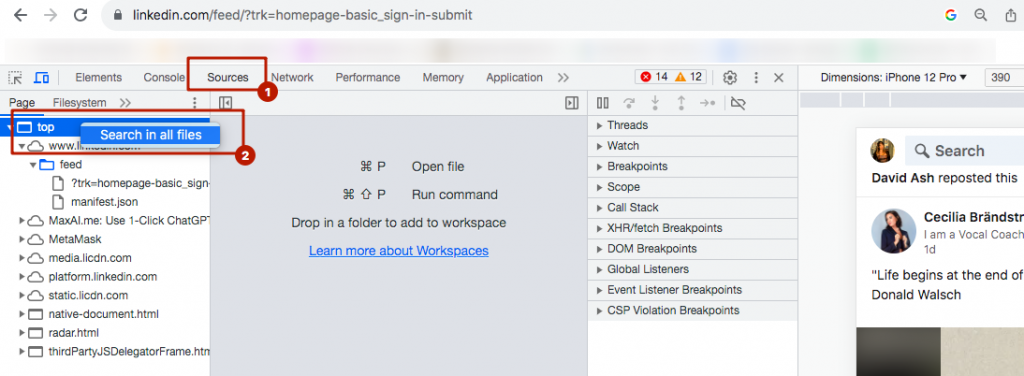
- Type the potentially dangerous extension ID into the search field and press Enter.
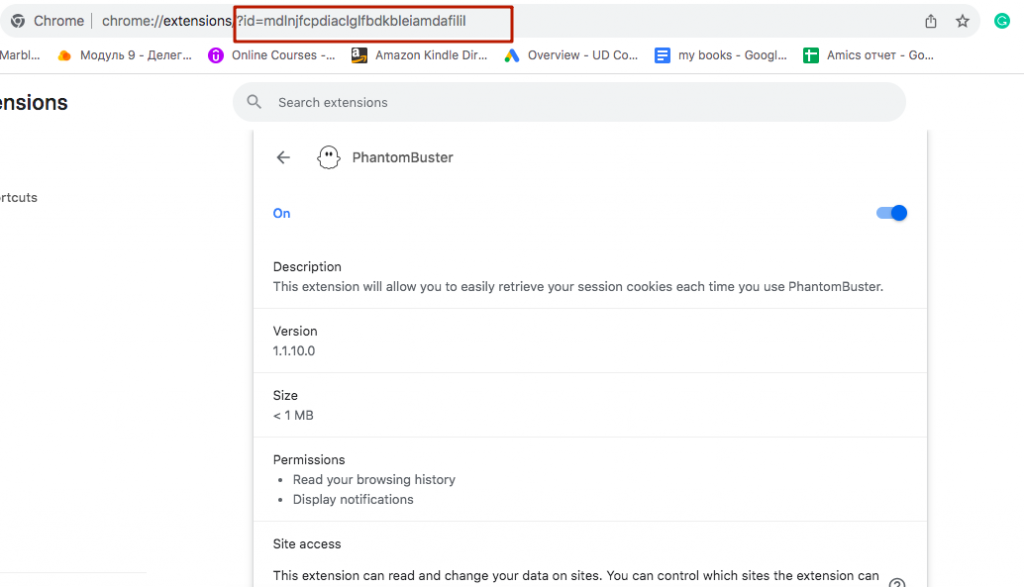
Tip: You can find the ID of each installed extension in Chrome by entering chrome://extensions/ in the browser’s address bar and then copying it from the search bar.
For example, we installed PhantomBuster, one of the risky extensions for automating LinkedIn that monitors the social network (and we added it to our list). We then copied its ID as shown in the example below.
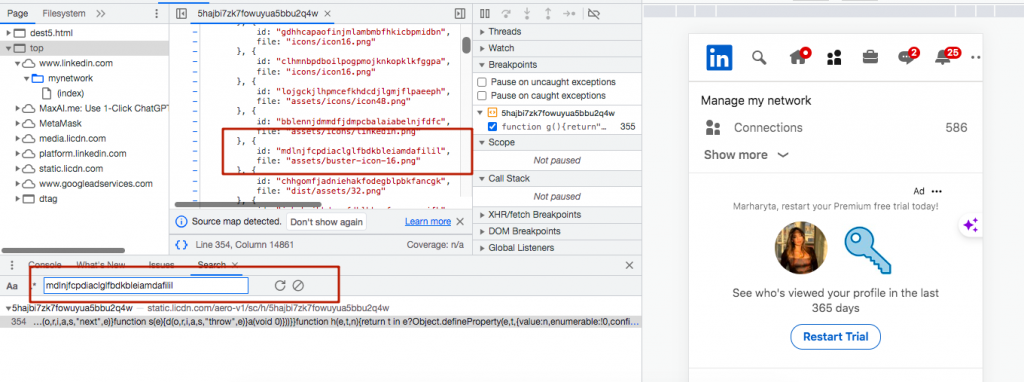
Finally: Click on the search results, and you’ll see that on this LinkedIn page, the algorithm detects the extension based on its ID.
As seen in the image below, by copying the PhantomBuster ID, we can observe that its files are visible on your LinkedIn profile. It’s these kinds of traces that can lead to a warning, even though we haven’t initiated any automated actions yet and have simply installed the extension.
If you are using Windows, you will see a similar interface as shown in the image below.
Bonus: Check if LinkedIn is detecting your Chrome Extensions
1. Open Notepad for Windows or TextEdit for Mac.
Tip: Do not use Google Sheets, MS Excel, MS Word, or other text editors for this, as the paste may not work correctly.
2. Open Chrome where LinkedIn is normally used.
3. Open this document.
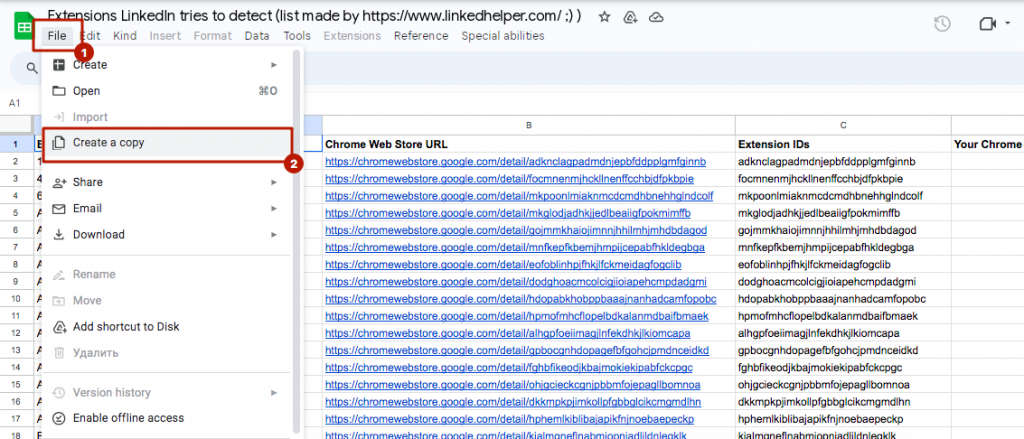
4. Make a copy of the document (as shown below) so that you can add the list of your extensions. Close the original doc.
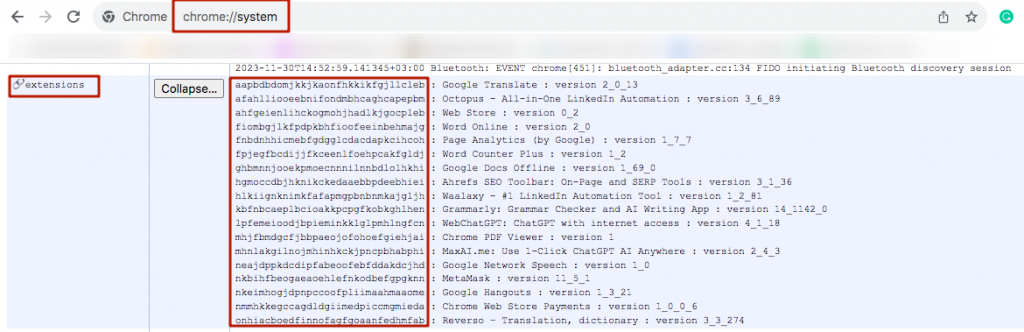
5. Open the link chrome://system/ in your browser in the new tab.
6. Expand the list of extensions.
7. Carefully select the list of IDs and names of these extensions and copy.
Note: If you capture other elements, the paste may be incorrect.
8. Paste it into Notepad or TextEdit.
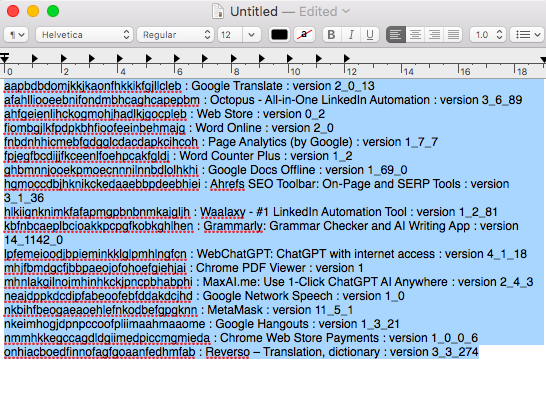
9. Select this data again in your Notepad.
Important: Copy it from Notepad. This is required to ensure that when pasting into Google Docs spreadsheet, the list is broken into rows, not pasted in one cell.
10. Open the copied Google document. Click on the cell “Your Chrome extension IDs,” and paste the list of extensions copied from Notepad.
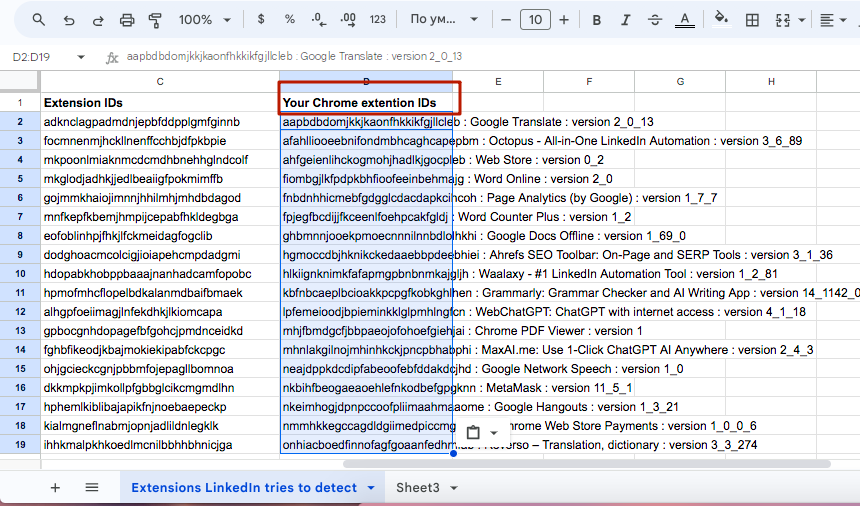
It should be inserted row by row as in the image.
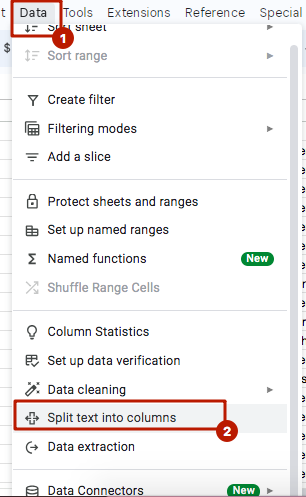
11. Select the column with the pasted data that we created in the previous step.
12. Go to Data > Split text to columns > choose “:” as the separator.
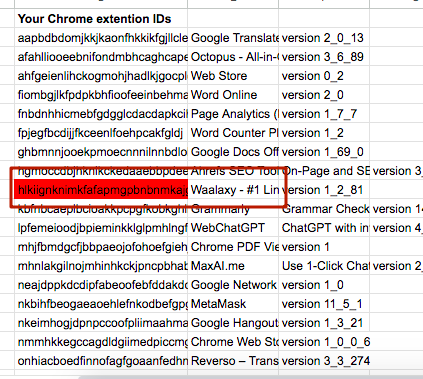
13. Extensions that LinkedIn is attempting to detect and that are installed in Chrome are highlighted in red.
Tip: If there are too many red-highlighted rows, you can filter the column by color. Microsoft Support – Filter by Font Color, Cell Color, or Icon Sets.
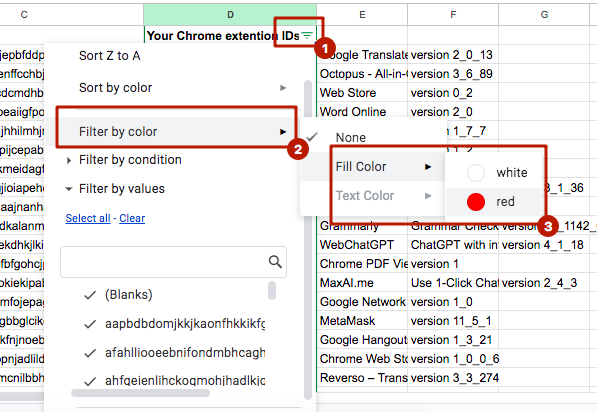
In the end, only potentially risky extensions will remain on your screen.
Hot takes about LinkedIn automation tools to escape a warning
Potentially risky Chrome extensions
If you want to find emails on LinkedIn with a Chrome extension, think twice! Even innocuously installed Chrome extensions carry potential risks, as LinkedIn actively monitors their presence. This surveillance means that using extensions, even for seemingly benign tasks, could lead to warnings or other consequences.
Warnings beyond Chrome extensions
LinkedIn warnings aren’t limited to issues with Chrome extensions alone. Engaging in certain manual activities that deviate from natural user behavior can also trigger warnings. For instance:
- High volume invitations: Sending an unusually high number of connection invitations per day, especially from a new account, may raise flags.
- Bulk URL invitations: Pasting URLs of numerous user profiles (even 50 per day) and sending invitations, particularly outside of regular search behavior, can be deemed unnatural.
Safety of Linked Helper
Linked Helper stands out as a safe tool for LinkedIn automation for several key reasons:
- Not an extension: Unlike traditional Chrome extensions, Linked Helper operates as standalone software, avoiding some of the detection challenges associated with extensions.
- Non-intrusive: It doesn’t embed any visible elements on LinkedIn pages, maintaining a discreet presence during automation.
- Strategic time-outs: Linked Helper incorporates various time-outs in its operations, mimicking human-like interaction patterns rather than rapid, automated actions.
- Fingerprint changes: The tool regularly changes its digital fingerprint, enhancing its ability to evade detection by LinkedIn’s monitoring systems.
In summary, while the use of Chrome extensions and manual activities can pose risks on LinkedIn, Linked Helper is designed with features that prioritize user safety by minimizing the likelihood of detection and warnings.